Modernize your SOC with an Intelligent SIEM + SOAR solution
While hackers continually innovate to become more elusive and destructive, cybersecurity cannot afford to remain static. With the proliferation of new devices, cloud databases, apps, hybrid infra models, multinational workforces, and complicated IT infrastructures, it is difficult for businesses to monitor and automate security processes. It is imperative that the Security Operations Center be redesigned (SOC).
Traditional Security Information and Event Management (SIEM) technologies have drawbacks such as high initial cost and maintenance, skills shortages, limited support, complicated pricing, compromised data collecting, and a large number of false positives with fewer relevant warnings. (Automated Security Orchestration and Response) SOAR solutions may assist your IT security team in enhancing and accelerating its incident response, a crucial aspect of contemporary cybersecurity. SOAR enables enterprises to collect and analyse security-related information and events from several sources, including SIEM. SOAR can efficiently automate security investigations, threat hunting, and remediation using this data.
More than
On average
Globally
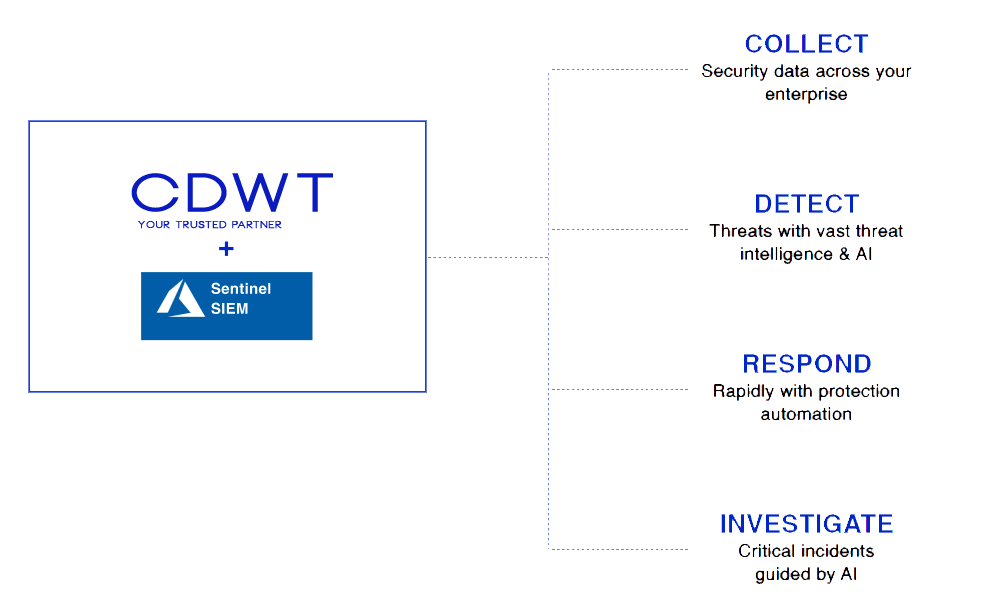
Enter Microsoft Azure Sentinel
Microsoft Azure Sentinel is a cloud-native, scalable SIEM + SOAR solution. Built-in AI, security analytics, configurable alert rules, and automated playbooks enable it to gather, identify, analyse, and react in real time. Implementing a cloud-based SIEM technology with integrated AI to analyse a vast number of data from apps, users, devices, and servers on any platform is one of the most cost-effective ways to do so. Azure Sentinel is a platform that enables enterprises to develop unique insights, threat intelligence, and detection models using machine learning.
Azure Sentinel allows you to:
Optimal Security solutions integrate Artificial Intelligence,Threat Analysis, and Automation.
Effectively safeguard your network, infrastructure, data, and apps on Microsoft Azure.
Investigate potential security breaches and collect forensic evidence in order to avert contemporary cyber dangers.
Our Managed Security Services for Azure Sentinel enable you to use Microsoft’s AI-powered technologies to enhance and streamline your security environment. During the engagement, our security specialists will cover all important aspects of your SOC, including the adoption of new technologies or procedures.

Azure Sentinel Security: From Reactive to Proactive
Integration of Azure Security Center and Azure Sentinel with your Security operations allows
Continuous discovery of flaws and configuration errors
Prioritize remediation depending on business context and the dynamic threat environment.
Identify the Machine-level vulnerabilities during event investigations
Correlation of Endpoint vulnerabilities
Detection and Response (EDR) alerts to provide breach-related information.
Integrated remediation procedures with Microsoft Intune and Microsoft
System Center Configuration Manager operations
SIEM and SOAR Implementation, Administration, and Training
Companies see SIEM and SOAR solutions as the cornerstones of their security teams’ ability to monitor network activity.
When it comes to analysing, installing, and maintaining SIEM/SOAR products, we often find that enterprises suffer with the following critical issues:
Principal Problems Facing Businesses
CDWT has installed Microsoft Azure Sentinel for the following client domains:
Banks and Financial institutions
Large Government Organizations
Healthcare giants
Large Manufacturers
Retail Business
Communication
Microsoft Azure Sentinel Deployment and Management Expertise from CDW
CDWT’s Azure Sentinel security expertise includes the creation of bespoke alert rules and automated playbooks to identify attacks in your environment in real time. CDWT simplifies and reduces the cost of implementing Azure Sentinel by gaining a grasp of your needs and the aspects you need to remain constant with enhanced capabilities.
Collect client needs and give upfront cost reductions from using Sentinel.
Use Case creation to improve customer visibility in the cloud environment
Examine log types and devices, both on-premises and in the cloud, and determine the proper data sources required to support use cases and the cloud migration.
Contribute to the log on-boarding activity
Creating and Configuring Sentinel and Log Data Onboarding Using Native and Custom Sentinel Connectors
Configuring dashboards and alerts
Creation of Threat Hunting templates and notification circumstances
The creation of playbooks that automatically run when an alert is triggered.
Knowledge transfer, detection and reaction training, and the generation of customer-use documents.
Conduct Incident management with a focus on Root cause analysis and mitigation.
Provide a weekly and monthly review of the security posture and advancements, along with information that can be used to enhance the security posture.
Technical account manager from the Security Operations Center (SOC) who is well familiar with the client's infrastructure. Auto-remediation of incidents in minutes without human interaction, which decreases incident response SLA and reduces total staffing costs.
On-demand availability of detailed forensics Team of threat intelligence professionals undertaking threat hunting.
Recommendations based on threat modelling and a comprehensive knowledge of infrastructure. Even for apps that cannot send logs, custom data collecting is supported. Creating bespoke parsers for even unstructured logs.
Workshop on Azure Sentinel Proof of concept
The Azure Sentinel Workshop is provided at no cost to you as an investment in your success. Register your organisation for a tailored one-on-one Workshop on Microsoft Azure Sentinel.
Workshop Objectives
Obtain the necessary information to onboard Azure Sentinel, including a technology deployment roadmap. Plan and supply information to construct a business case for an Azure Sentinel production deployment, including a technical deployment plan.
Gain insight into risks to your Microsoft 365 cloud and on-premises systems spanning email, identity, and data in order to better identify, prioritise, and defend against possible cyber-attack vectors.
Assist you in comprehending how Microsoft 365 and Azure security technologies may assist you in mitigating and protecting against the dangers identified throughout this engagement.
Learn via hands-on experience how to identify and evaluate threats with Azure Sentinel. Learn how to automate your Security Operations in order to improve their efficacy.

Some easy steps to process!
Learn about the features and advantages of Azure Sentinel
Gain visibility into email, identity, and data risks.
Improve understanding, ranking, and mitigation of possible threat vectors
Create a customised deployment plan based on your environment and business and technological objectives.
Develop cooperative exploration and implementation plans


Rapid Advantage to you
Why CDWT?
As an Azure Expert MSP, we assist you in gaining a deeper understanding of Azure Sentinel’s capabilities, determining whether it can alleviate your security pain points, and determining whether managed cybersecurity services – for both detection and incident response – can quickly and cost-effectively improve your security posture.
Security frameworks using the MITRE ATT&CK, CIS Critical Security Controls, and other methodologies
Over 2,000 Cloud-certified (on several public cloud platforms) professionals
Cyber Security Incident and Response Team (CSIRT) group at CDWT
With decades of expertise in assessing threat information streams, security analysts and threat specialists can safeguard vast and complicated settings.
Threat Intelligence driven by industry-leading platforms like Microsoft, OSINT, STIX&TAXI, MISP, etc. and CDWT Threat specialists.
Expertise in building and administering strong SIEM and SOAR - assisting organisations in proactively assessing vulnerabilities and automating and accelerating incident response.
Comprehensive 24-hour-a-day monitoring system
A single point of contact for resolving any security issues
Azure Sentinel – FAQ’s
Azure Sentinel analyses enormous amounts of data from on-premises or cloud-based users, apps, servers, and devices.
Sentinel is connected with Microsoft services, such as Azure Security Center, Azure Active Directory, and Microsoft 365, as well as third-party connectors.
Built-in alert rules and the flexibility to personalise rules based on the requirements of your organisation, using a custom alert wizard.
To uncover illicit SSH access, machine learning skills that recognise questionable logins across Microsoft identity services are required.
Predictable and adaptable billing methods with pay-as-you-go pricing choices
Graphical interfaces that enable users to visualise and navigate the connections between entities such as users, assets, applications, or URLs, and quickly comprehend the scope and impact of any security incident based on suspicious activities such as logins, data transfers, or application usage, etc.
Due to the novel actions and playbooks offered in Azure Logic Apps, incident automation and remediation are easier.





















