Managed Endpoint Detection and Response Services
Extend deep threat visibility to endpoint environments. Conduct sophisticated analysis and forensics. Prevent, Detect, and Manage All Endpoint Threats
Endpoint Security: Shielding the first defensive line
With the avalanche of end-user electronics connected to organisational networks today, including smartphones, PCs, laptops, tablets, routers, printers, accessories, and Internet of Things (IoT) devices, the need for specialised security frameworks addressing this vast front-line perimeter appears to be imperative. However, the truth is less optimistic. Typically, end-user devices connected to an organization’s IT mesh are poorly secured by standard antivirus and anti-malware software. This creates a gaping breach through which fraudsters may infiltrate the company’s perimeters, conceal themselves from rule-based regular inspections, and conduct catastrophically designed assaults.
Threat Detection and Response at the Endpoint (EDR)
Endpoint Detection and Response is a comprehensive solution suite that optimizes an organization’s endpoint environments end-to-end, including IoT networks, edge environments, employee devices, terminals, accessories, web-host assets and applications, and remote work devices. EDR systems combine deep threat detection, analysis, and auto-response activities to existing Endpoint Protection Platforms to provide a comprehensive cyber protection for endpoint settings. The primary features of a deployed EDR system include:
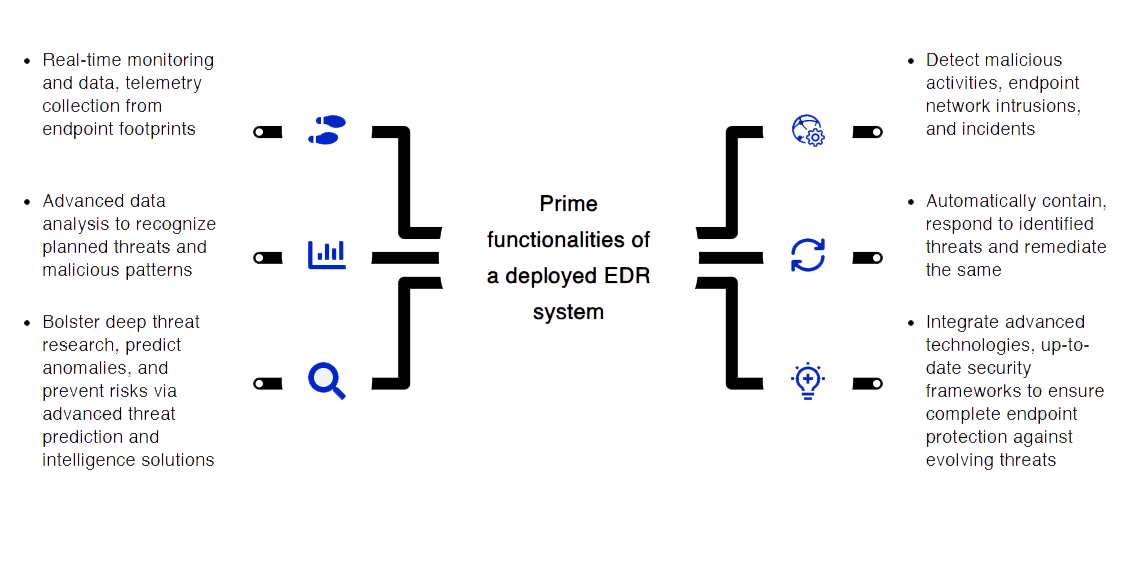
Examine the Revolutionary Benefits of CDWT Managed Endpoint Detection and Response (EDR)
- Threat Visibility and Monitoring
- Timely Attack Detection
- Attack Analysis
- Manual Intervention
- Incident Response
- Organization Security Maturity
- Compliance Management
- Custom Capabilities
















CDWT Managed Endpoint Detection and Response (EDR)
Beyond Conventional Endpoint Protection (EPP) and Virus Protection Capabilities
As previously stated, classic EPP solutions are mostly preventive, and their methodologies are often signature-based: recognising risks based on the signatures of known files for newly identified vulnerabilities.
Advanced managed Endpoint Detection and Response (EDR) platform from CDWT combines next-generation antivirus and antimalware capabilities with real-time anomaly detection and alerting, forensic analysis, and auto-remediation. By evaluating every file execution and modification, registry change, network connection, and binary execution across all endpoints, the endpoint security solution boosts threat visibility beyond that of modern Endpoint Protection Platforms.
Antimalware and Antivirus Capabilities
-
Protection based on signatures and shielding with simplicity
-
Solid protection against recognised dangers
-
Objectives for the utilization of custom IT resources as a foundation
-
Prevention with Endpoint Protection Platform (EPP)
-
Device and Web Control
-
Patch Management
-
Data Encryption
-
Host Intrusion Security
-
System Lockdown
-
Enterprise Mobility Management
-
Vulnerability Assessment
-
Application Control
-
Firewall Management
-
Detect, Evaluate, and Respond Endpoint Detection and Response (EDR)
-
Centralized Remote Response
-
Forensic Data Aggregation
-
Remediation Capabilities
-
Suspicious Activity Validation
-
Response Automation
-
Threat Hunting
-
Real-time endpoint visibility
-
Incident Investigation and Containment
-
Real-time monitoring
-
Incident Investigation
-
Advanced Detection: Yara-rules, Sandboxing, IoC Scan, Threat Intelligence
-
CDWT End-to-end Managed Detection and Response Offerings
- Comprehensive Cyber Threat Monitoring across the Entire Endpoint Landscape
- Ingestion of Data and Telemetry
- Threat Hunting, Threat Research, and Intelligent Threat Detection
- Analysis of Threats and Incidents Utilizing Deep Security Analytics
- Threat Prevention and Patch Management with (EPP) Endpoint Protection Platform
End-to-end, round-the-clock deep threat monitoring of all endpoints, including user devices, cloud and network terminals, accessories, remote working appliances, IoT-Edge environments, smartphones and mobility solutions, PC-laptop-tablets, web assets and applications, and third-party devices, among others. Gain automatic alert management and optimization (to decrease alert fatigue), as well as insight into the risk posture of the whole company. Reduce drastically the manual reliance on security staff.
Integrate the endpoint security solution with internal, external, and mission-critical dataflows from all endpoints: user devices, cloud, and network terminals, accessories, remote working appliances, IoT-Edge environments, smartphones and mobility solutions, PC-laptop-tablets, web assets and applications, etc. EDR offers data input and monitoring from all endpoint networks, extensive forensic data aggregation, in-depth security analysis by means of intelligent analytics, and threat research and investigation capabilities. Enable the development of threat databases, heuristic analyses, and reputation services.
Advanced Managed Endpoint Detection and Response (EDR) security solution from CDWT incorporates superior threat intelligence for threat research, detection, and hunting. Predict and locate dangers hiding behind the most basic, perimeter endpoint layers or through normal rule-based assessments without the assistance of security experts. Analyze apparently harmless codes to determine whether they are part of future, larger assaults. Integrate suspicious activity validation and Advanced Threat Protection features, including Yara-rules, SandBoxing, IoC scan, Threat Intelligence, Anti-rootkit, Mobile Threat Protection, Behavioral Detection, and Ransomware prevention.
Automatically assess threats at endpoints and risk-prone use-cases in conjunction with threat monitoring and threat hunting in order to organise them into appropriate incident groups using advanced security analytics. The EDR security system enables the bundling of warnings from endpoints, minimising alert fatigue for security teams and aiding the Security Response Team in gaining sophisticated, real-time threat information for making educated decisions. EDR technologies provide seamless support for enhanced forensic data aggregation, in-depth security analysis using intelligent analytics, and threat investigation and research capabilities. Enable the development of threat databases, behavioural and heuristic analyses, and reputation services.
CDWT Endpoint Security capabilities and EDR tools provide integration of all Endpoint Protection Platform functionality as well as comprehensive Detection and Response operations. The same holds true for ML-based threat defences, improved Patch Management, Data Security, Host Asset intrusion prevention, and more, all with a minimal resource footprint. Integrate intelligent firewalls and get comprehensive threat protection for all endpoint devices and applications:
- Mobile devices, PCs, laptops, tablets, remote work devices, accessories, web assets and applications, IoT-Edge devices, etc.
- Patch Management
- Coding of Information
- Prevention of Attacks Against Host Assets
- System Lockdowns
- Enterprise Mobility Management
- Vulnerability Evaluation
- Application Control and Risk Avoidance
- Firewall Management
- Integrating Security Operations Centre (SOC)
- Threat Mitigation and Endpoint Security Response Automation
- Zero Trust Architectural Design
- Compliance Administration
- Solutions for Intelligence on Danger
The CDWT EDR technology integrates smoothly with an organization's unified SOC environment and security analysts. As a dedicated Security Operations Center team for your endpoint settings, CDWT provides end-to-end threat management and facilitates the deployment of innovative cybersecurity frameworks, techniques, and intelligent solutions.
- Integrated SIEM-SOAR
- Identity and Access Administration
- Superior Threat Protection (ATP)
- 24/7 Surveillance and Incident Response
- Console for centralised security management
- Incident Restoration and Rehabilitation
- Log Collection and Administration
- Cause and Effect Analysis
- Management of Vulnerabilities and Preventive Maintenance
- Solutions for Cybersecurity Powered by AI
- Alert Management
- Conformity Audits
- Dashboarding and Reporting
- Superior Penetration Tests
Achieve the lowest Mean Time to Detect and Mean Time to Repair for all endpoint threats with CDWT's cloud-based Advanced Managed Endpoint Detection and Response technology. Upon detecting and analysing an endpoint threat, automatically contain the malicious software's effect to avoid large-scale losses. With sophisticated threat mitigation, initiate auto-response activities. Obtain centralised remote response capabilities. With CDWT EDR, your endpoints will be fully protected against threat and suspicious activity detection, analysis, and remediation.
Advanced Managed Endpoint Detection and Response will fortify your Zero Trust security platform and architecture. Utilize real-time threat hunting, detection, and auto-response to prevent Zero-Day exploits. Protect endpoints from fileless and premeditated assaults. Develop impregnable resistance against Ransomware and Malware assaults. Integrate the most effective endpoint security approach in order to defend against an ever-changing threat environment.
Compliance-related problems can result in significant IT process gaps inside a business. This might be an enticing offer for hackers. As part of the expanded MDR package, CDWT's compliant-ready products guarantee that client facilities comply with data localization-residency legislation, national regulations, local compliances, and international certifications. Compliance adherences, including but not limited to:
- IRAP
- Bank Negara
- Central Bank of Oman
- SAMA
- FINMA
- UAE Compliances
- RBI
- MAS
- OJK
- GDPR
- CSA
- PCI-DSS
- HIPAA
- GXP
- International Standards: ISO-27001, ISO-27017, ISO-27018, ISO-22301, ISO-
20000, AICPA SOC, AICPA SOC2
Enable enhanced threat intelligence capabilities on endpoints and at the perimeter. Connect intelligent analytics from many sources, provide bespoke segregation capabilities, enhance threat hunting with contextual indications, and integrate core corporate security solutions in a smooth manner (MDR, SIEM, SOAR, etc). IP/Domain Reputation, File Reputation, CWPP, CSPM, CASB, and Phishing-malware-ransomware feeds from many sources are consolidated. Utilize the patented Self Healing or Preventive Maintenance Platform to not only decrease Meantime to Detect and Meantime to Repair, but also eliminate hazards via enhanced risk prediction and automated risk healing procedures.





