SOAR – Managed Security Orchestration Automation and Response Services
Integrate multiple, advanced security solutions. Automate SecOps workflows. Fast-track Incident Response with Fail-proof efficiency
SOAR Platforms: The Ark of Noah during the Cyber Flood?
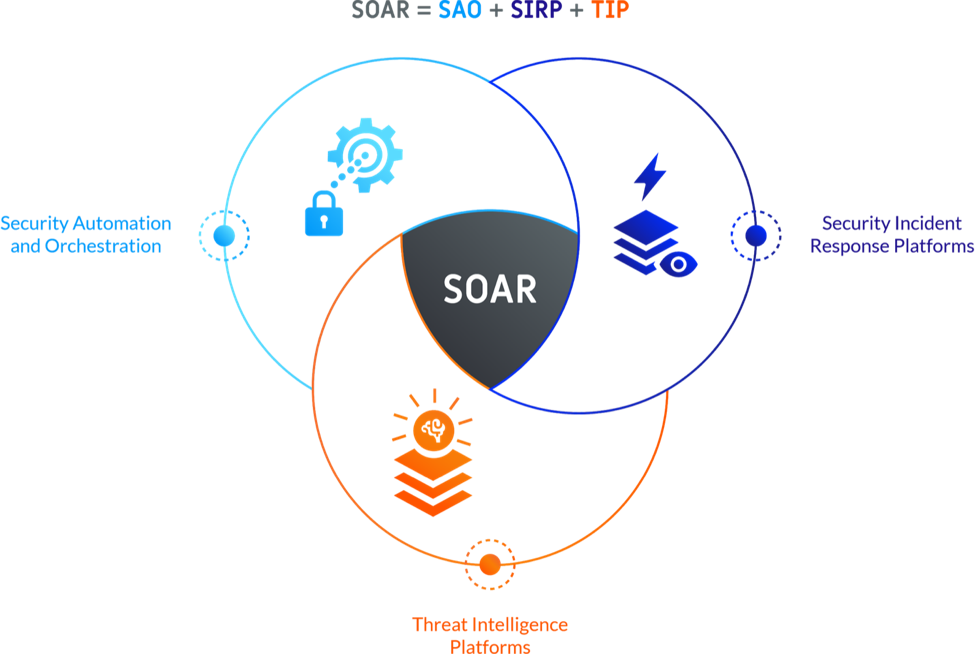
SOAR, or Security Orchestration, Automation, and Response, solutions have gained great popularity worldwide since Gartner popularized the phrase a few years ago. Simply described, it is a security software stack that integrates diverse security apps, tools, systems, APIs, and their respective features into a single, universal dashboard. The solution automates additional security management activities associated with integrated solutions, such as ultra-agile, efficient reaction actions to any identified threat or malicious behaviour across the whole IT environment. A survey indicates that by 2021, more than 15% of firms with at least a five-person security team will have used a SOAR platform. This is much greater than the 2019 rate of 1%.
SOAR systems provide the essential answer to combine corporate SecOps and threat response in a world inundated with dynamic threats and consequently various non-synchronous security tools-frameworks.
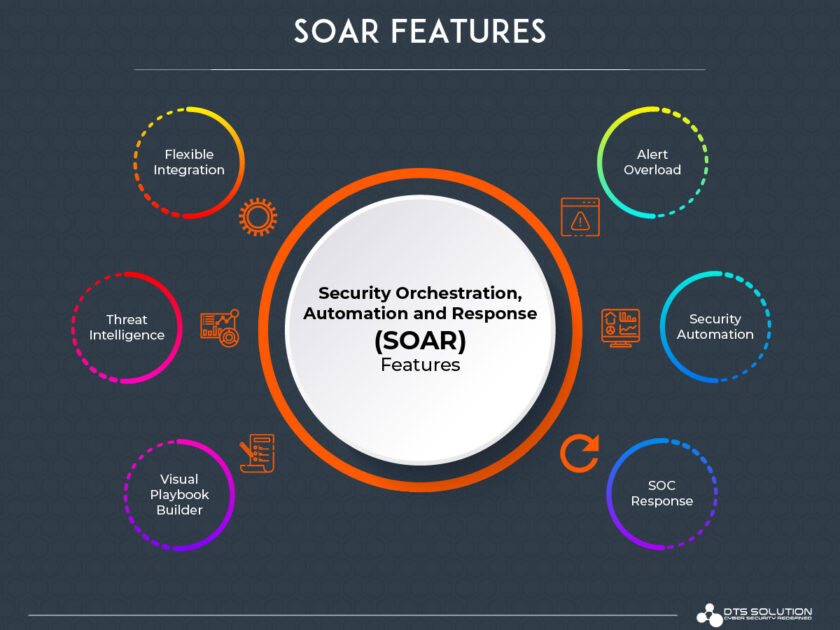
SOAR Map
Security Coordination
Incorporates diverse internal and external security tools, applications, APIs, and systems, such as vulnerability scanners, endpoint detectors, incident management systems, SIEM platforms, intrusion management tools, Log/Telemetry collection, and security analytics solutions, onto a centralized, universally administered SOAR platform.
Security Technology
Utilizes process playbooks to automate security processes, including mal checks, mail threats, scanning, auditing, threat hunting, network flow checks, dataflow checks, pattern-based attack monitoring, etc. Integrates sophisticated Threat Intelligence to interpret analytical findings, evaluate vulnerabilities, and trigger threat mitigation methods
Security Measures
Offers quick, automated response to low-level, pattern-based threats. Initiates extremely effective reaction processes, provides advanced insights, and provides assistance to SOC teams for advanced threat mitigation. Shares post-mitigation reports with extensive, insightful information to improve future threat management.
SOAR Integration Benefits for: Organizational SecOps
- Rapid Threat Identification and Effective Response
- Rapid Threat Identification and Effective Response Superior Threat Analysis
- Information Gathering and Security Analytic
- Streamlined Workflow Management
- Alert Fatigue Management
- Communication and Coordination
- Cost reductions
- Intelligence Regarding Threats
















End-to-End Security Orchestration Automation and Response (SOAR) Services from CDWT
- Security Orchestration Management
- Security Automation for Operations
- Management of Managed Security and Incident Response
- Extensive Threat Detection
- SIEM Implementation
Conducts a comprehensive examination, evaluation, and integration of all security tools, technologies, systems, applications, and APIs distributed across the IT landscape of the enterprise into the newly built SOAR platform. Provides total insight into the risk position of the company via a single pane of glass.
Deploys, manages, and consults on the creation of custom automated playbooks or workbooks to automate common security workflows, such as log collection, event checks, breach audits, threat analysis, vulnerability assessments, phishing attacks or any other malicious activity audits, monitoring, alerts management, etc. With all repetitious security processes and operations completely automated, including automated replies, the client's SOC and security teams may focus on more advanced and strategic endeavours.
Ensures comprehensive oversight and management of the incident response operations of a SOC platform. Using playbooks, SOAR systems automatically initiate extremely effective incident response activities. This comprises frequent threats, assaults based on previous patterns, and low- and moderate-level suspicious activity. Analyzes, filters, and transmits created warnings (through SIEM or other installed security solutions) for remediation of advanced threats. Collaborates with client security teams to provide threat response statuses and reports, actionable insights for end-to-end vulnerability management, and strategic inputs to strengthen future security threats response capabilities.
The SOAR platform and SOAR tools combine with sophisticated, intelligent threat hunting technologies in order to develop, administrate, and react automatically to deep-level threats. Through the use of streamlined connections, the former might also be integrated with cloud-native threat detection and monitoring platforms. This enables the SOAR platform to quickly identify threats across the organization's heterogeneous IT ecosystems and begin instant threat analysis and response operations.
Obtain 24/7, real-time incident management, including threat monitoring, detection, analysis, and reaction management, when SOAR is linked to the SIEM platform of the enterprise. Gain insight into all risks and threat potential throughout the whole IT landscape, including data, apps, networks, computing infrastructure, datacenter assets, databases, middleware-OS-platforms-architectures, cloud environments, and third-party integrations. Integrate sophisticated analytics and intelligent cybersecurity solutions in order to foresee threats, provide end-to-end health monitoring, strengthen system security standards, and implement rapid threat remediation.
- Ingestion of Data and Security Analytics
- Collaboration of SOC
- Compliance Administration
- Cloud Incident Management
- Intelligence Regarding Threats
Integrates data, telemetry, and log information from many sources through SIEM systems, monitoring tools, event management and correlation apps, security solutions, etc. SOAR solutions use cutting-edge AI, ML, Behaviour Analytics, and other sophisticated analytical frameworks to provide the internal security team with in-depth risk analysis, security event insights, and strategic recommendations.
The SOAR package integrates smoothly with a company's SOC activities. As a managed SOAR and SOC (Security Operations Center) services provider, CDWT acts as an extended Cybersecurity Incident and Response Team (CSIRT) to your security management, delivers the entire monitoring and threat management work with ease, and aids your organisation in adopting innovative cybersecurity frameworks, methodologies, and intelligent solutions for modern security management.
Utilize the SOAR's integrated solutions and automated analytic methods to conduct in-depth study and auditing of Security Operations. Compliance-related problems can result in significant IT process gaps inside a business. This might be an enticing offer for hackers. The compliant-ready services provided by CDWT guarantee that client facilities comply with data localization-residency legislation, national regulations, local compliances, and international certifications. Compliance adherences, including but not limited to:
- IRAP
- Bank Negara
- Central Bank of Oman
- SAMA
- FINMA
- UAE Compliances
- RBI
- MAS
- OJK
- GDPR
- CSA
- PCI-DSS
- HIPAA
- GXP
- International Standards: ISO-27001, ISO-27017, ISO-27018, ISO-22301, ISO-20000, AICPA SOC, AICPA SOC2
Synchronize the adopted SOAR solution with private, public, hybrid, and multicloud systems for top cloud platforms, including AWS, GCP, Azure, Oracle Cloud Infrastructure, IBM Cloud, and others. Protect your SaaS applications, PaaS infrastructures, and IaaS processes with the selected SOAR platform in order to acquire robust threat/incident investigation, monitoring, analysis, and response capabilities for cloud workloads. Connect SOAR with cloud log management portals, monitoring, and native security technologies to get a more flexible, comprehensive, and sophisticated cloud security solution.
Enhance intelligent cybersecurity management skills with the selected SOAR system, focusing on threat detection, analysis, and response features. IP/Domain Reputation, File Reputation, CWPP, CSPM, CASB, Phishing-malware-ransomware feeds, and IT assets management should be consolidated. Obtain intelligent, streamlined process automation for security operations. Utilize the patented Self Healing or Preventive Maintenance Platform to not only decrease Meantime to Detect and Meantime to Repair, but also eliminate hazards via enhanced risk prediction and automated risk healing procedures. Under the guidance of a world-class SOC team, modernize cybersecurity administration by using AI-driven technologies.
Cloud-native Intelligent SIEM-SOAR Solution for End-to-End Threat Management is Microsoft Azure Sentinel.
Azure Sentinel, along with Windows Defender, Microsoft Cloud App Security, and others, is the jewel in the crown of Microsoft’s sophisticated cloud security products. Microsoft Azure Sentinel is an intelligent cloud-native Security Information and Event Management (SIEM) and Security Orchestration and Automation Response (SOAR) solution for end-to-end IT security management.
The platform provides a security monitoring, threat/alert detection, proactive remediation, and intelligent security analytics solution applicable to all IT assets and resources, including computing assets, devices, servers, databases, datacenters, platforms, architectures, applications, networks, and Edge-IoT environments, among others.
Azure Sentinel links effortlessly to other security technologies, such as Windows Defender, Azure Cloud Apps Security, Azure Monitor, Log Analytics and Logic Apps, Azure AD, MITRE Frameworks for advanced threat hunting, automation tools, and more.
Features Of Azure Sentinel
Data Gathering
Effortless gathering of data from IT devices and resources, including as users, apps, hardware, and networks, on-premises as well as from numerous cloud platforms linked to Azure. Integrate Azure-native and non-Microsoft security solutions with ease to create a more robust IT security ecosystem backed by Sentinel.
Global Observability and Analytics
Extend security analytics and real-time insight throughout the whole IT ecosystem. Correlate alarms into events to initiate automatic operations, implement Anomaly Detection based on Machine Learning, map network and user activity data, and make educated cybersecurity management judgments.
Superior Threat Investigation and Hunting
Acquire dynamic, intuitive, and comprehensive threat analysis skills across all IT resources and different cloud, edge, and IoT ecosystems. Prepare unique warning criteria, discover risk alerts and threats previously ignored, and engage in advanced threat hunting using the capabilities of Azure Sentinel's artificial intelligence. Utilize Azure Sentinel's robust hunting search and query capabilities supported by the MITRE architecture to proactively explore the IT landscape of the enterprise for threats.
Utilizing Security Automation and Orchestration for Threat Mitigation
Azure Sentinel's cognitive security automation and orchestration capabilities automate typical threat management operations across the enterprise. Integrate Sentinel with Logic Apps, Logic Analytics, Azure Functions, 200+ connectors for other Azure services, and corporate tools like as Jira, Zendesk, Slack, and Microsoft Teams, among others, to unleash end-to-end automated security management.
CDWT Azure Sentinel Managed Services
Azure Sentinel Deployment
-
Perform a comprehensive assessment of the client's IT environment, processes, and dataflows, including alerts and modifications.
-
Collect client specifications and propose upfront cost savings for using Sentinel.
-
Use Case creation to improve customer visibility in the cloud environment
-
Analyze log types and devices, both on-premises and in the cloud, and determine the appropriate data sources required to support use cases and the migration to the cloud.
-
Assist in onboarding log activities
-
Configuring Sentinel and importing log data using both native and custom Sentinel connectors.
-
Configuring dashboards and alerts
-
Creation of Threat Hunting templates and notification circumstances
-
The creation of playbooks that automatically run when an alert is triggered.
-
Knowledge transfer, training in detection and response, and document development for client usage.
-
Azure Sentinel Management
-
Continuous Fine-Tuning of Infrastructure-Specific ATT&CK-Based Rules and Compliance Policies
-
Conduct Incident management with a focus on Root cause analysis and mitigation.
-
Provide weekly and monthly updates on the security posture and developments, along with information that may be used to enhance the security posture.
-
Technical account manager from the SOC with comprehensive knowledge of the client's infrastructure. Auto-remediation of incidents in minutes without human participation decreases incident response SLA and reduces total staffing costs.
-
The detailed forensics service provided an on-demand team of cyber threat intelligence specialists that conducted threat hunting.
-
Recommendations based on threat modelling and a comprehensive knowledge of infrastructure. Even for apps that cannot send logs, custom data collecting is supported. Creating bespoke parsers for even unstructured logs.
-
Continual identification of vulnerabilities and misconfigurations in conjunction with real-time business processes and capabilities.
-
Detection and Response (EDR) notifications to provide breach information on a global scale. Correlation of Endpoint asset vulnerabilities
-
During in-depth incident investigations, identify Machine-level vulnerabilities.
-
Based on the business context and the ever-changing threat environment, prioritise cleanup. Integrated remediation procedures with Microsoft Intune and Microsoft
-